2020 Development Cycle
Following the content guidance from the various Authority Documents1, contribution through a centralized API roughly follows the data model shown below:
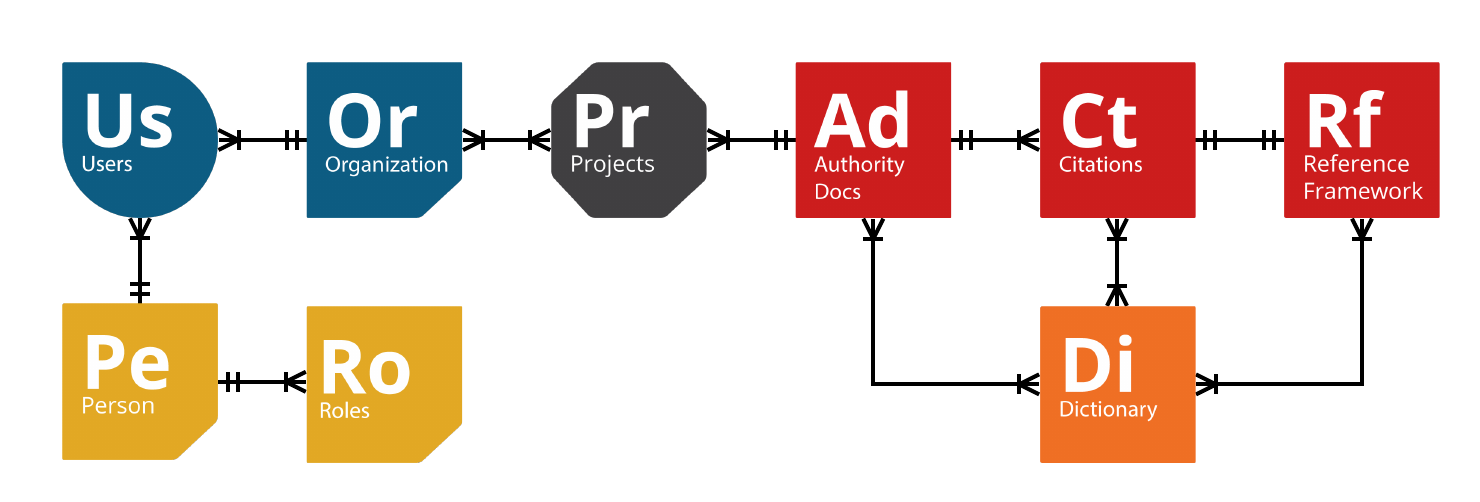
Breaking the data model down
For clarity, we will break the data model into its constituent parts, describing how a contribution would take place.
- A Disambiguated Person is assigned a
- Role of contributor (Author, Mapper, etc.), who is part of
- a Disambiguated Organization. That person wants to contribute a
- Project that contains an
- Authority Document (or as NIST OSCAL calls it a catalog) that has various
- Citations (or SWID entries, or catalog entries, or reference elements) that have identified
- Dictionary Terms (such as product names, tagged nouns or verbs) and a possible match to a
- Reference Control (or focus control or Common Control).
We will call this continuous process an entry.
A catalog of the following will be queryable via API:
- Authority Documents and entries,
- organizations, and
- contributors (and associated persons)
Furthermore, the API will allow disambiguated persons from disambiguated organizations to create entries.
In order to build out this data model and ensure that it works through a publicly published API, five steps need to be completed for each schema in the data model:
- A schema will be proposed for comment.
- The schema will be publicly distributed and discussion will be requested.
- When the discussion has reached its logical conclusion, the schema will be voted on and locked.
- Once the schema is locked, API building and testing will be undertaken, with alpha and beta versions of the API made available for testing and discussion.
- When the discussion has reached its logical conclusion, the API’s possible versions will be voted on and locked. Once locked it will be made publicly available.

This can be accomplished in a stair-step manner wherein we build out the schema and APIs from their logical progression as listed in the contribution scenario above. Once a schema has been voted on and locked, the next schema in the logical progression can be proposed.
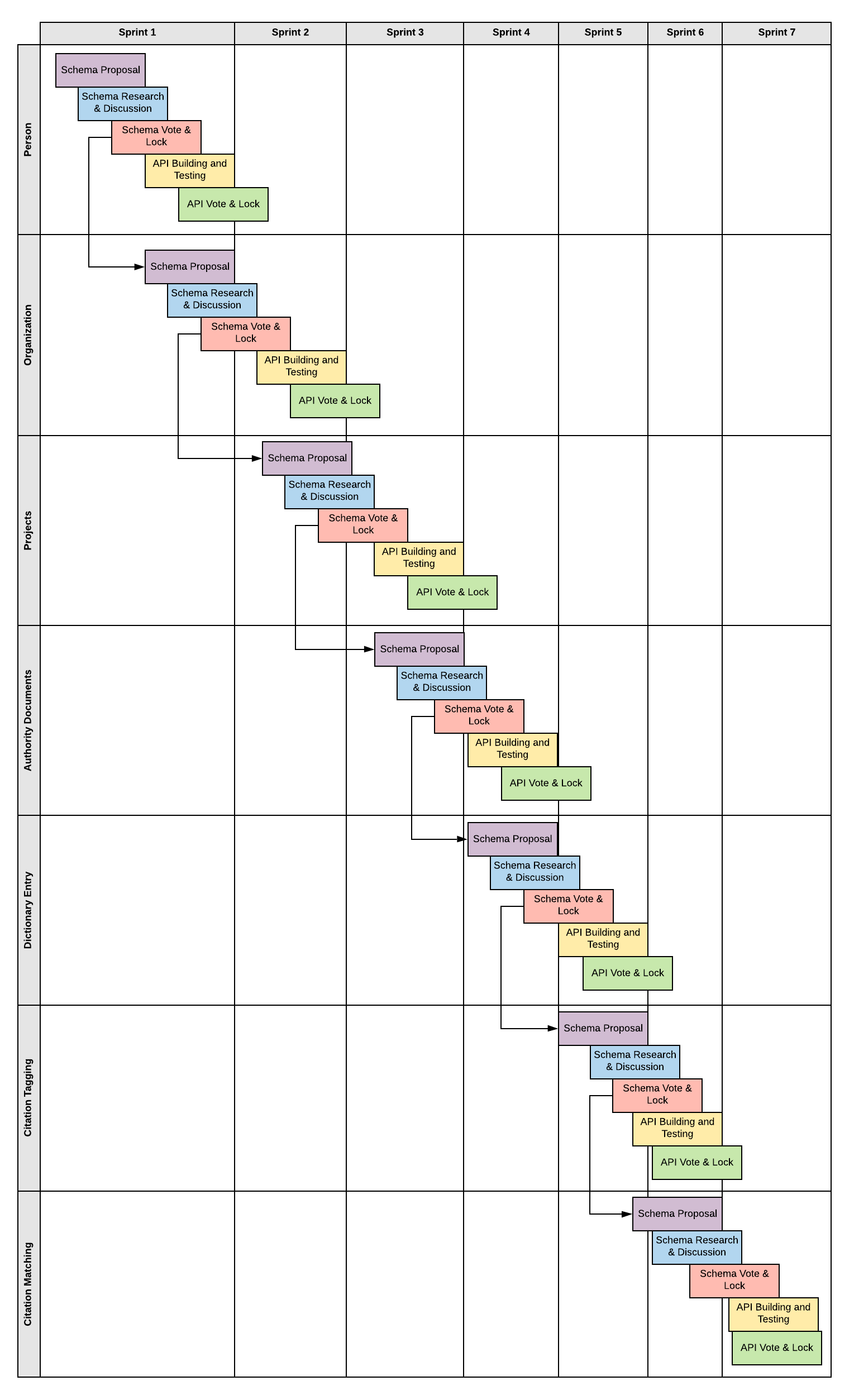
-
NIST’s Informative Reference Catalog, NIST’s Open Security Controls Assessment Language (OSCAL), TagVault.org’s Software Identification Tags (SWID Tags), SIGLEX, and content contributed by the Unified Compliance Framework ↩︎